There is a major vulnerability in a popular plugin with over 300,000 active installs: User Role Editor 4.24 and older.
The vulnerability allows any registered user to gain administrator access. For sites that have open registration, this is a serious security hole.
If you are running User Role Editor, upgrade to the newest version which is 4.25 immediately.
Looking at a diff of the newest plugin release, the author was checking if users have access to edit another user using the ‘current_user_can’ function and checking for the ‘edit_user’ (without an ‘s’ on the end) capability on a specific user ID. The green code below was added.
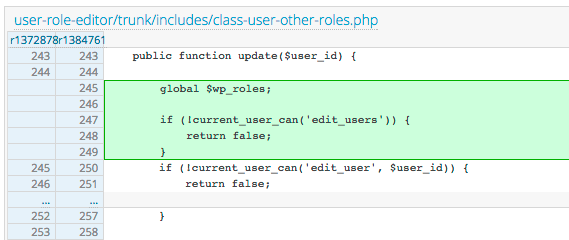
A user can edit themselves, and so sending data to the plugin that supplies the current user’s ID to this access check would bypass the check.
The fix released in version 4.25 (new code shown in green above) checks if the current user has the ‘edit_users’ capability which is a general access check that would fix this vulnerability.
The edit_user check that was being used is undocumented on the Roles wiki page, but it is used by WordPress core (in a secure way). So if you are using this check in your plugins, it is important to realize that it can be bypassed if used as a general access level check.
As always, please make sure that the rest of your plugins are at the newest version because we have seen several, less impactful vulnerabilities emerge during the past month.
Regards,
The Wordfence Team.
The post Vulnerability in User Role Editor – Users Can Become Admins appeared first on Wordfence.
