On this blog we write a lot about different vulnerabilities that could lead to site compromise. In our Learning Center we go deep on a myriad of important topics related to WordPress security. Our handy checklist, for example, includes 42 items you really should be paying attention to. But surely not all 42 items are equally important, right? In today’s post we dive into some very interesting data we gathered a couple of weeks ago in a survey, letting the facts tell us what matters most.
The question we asked in the survey was:
If you know how your site was compromised please describe how the attackers gained access.
The answers were free form text, so we manually categorized the answers. If the respondent expressed any doubt in their answer, we categorized them as uncertain.
Most Site Owners Don’t Know
Of the 1,032 survey respondents who answered this question, 61.5% didn’t know how the Attacker compromised their website. That is a not a huge surprise given that the large majority of respondents cleaned their sites themselves, but it is troubling. It is impossible to be confident that you have cleaned your site completely or that the vulnerability doesn’t still exist without knowing how the site was compromised in the first place.
For the site owners who did figure out how the attackers entered, here is what the breakdown looks like:
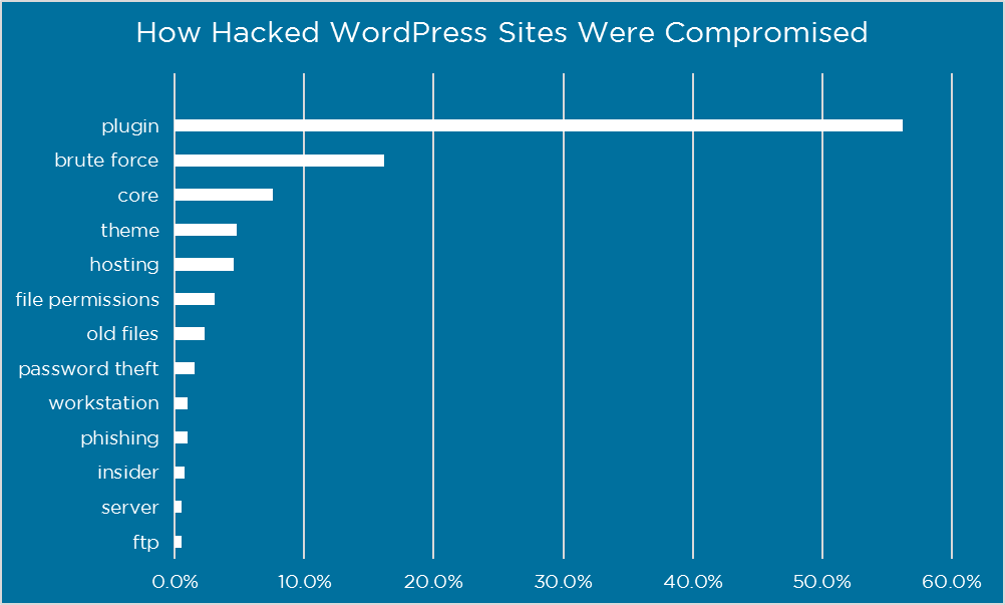
In the balance of this post we’re going to focus primarily on the top two risks. Because if you can protect yourself against plugin vulnerabilities and brute force attacks, you are accounting for over 70% of the problem.
Plugins Are Your Biggest Risk
Plugins play a big part in making WordPress as popular as it is today. As of this writing there are 43,719 plugins available for download in the official WordPress plugin directory. That is an incredible selection of plug and play software. But you obviously need to be careful with them, as plugin vulnerabilities represented 55.9% of the known entry points reported by respondents.
Some tips for avoiding plugin vulnerabilities:
Keep them updated
Reputable plugin authors fix vulnerabilities very quickly when discovered. By keeping them up to date you insure that you benefit from fixes before attackers can exploit them. We recommend that you check for updates at least weekly. In addition we recommend that you pay attention to the alerts generated by Wordfence scans. Wordfence alerts you when your plugins need to be updated.
Don’t use abandoned plugins
You are relying on the plugin developer to insure that their code is free of vulnerabilities. If they are no longer providing updates there is a high likelihood that there are vulnerabilities that have not been fixed. We recommend avoiding plugins that have not been updated in over 6 months. For plugins you have already installed we recommend you conduct an audit at least quarterly to make sure none of your plugins have been abandoned by their authors.
Only download plugins from reputable sites
If you are going to download plugins somewhere other than the official WordPress repository, you need to make sure the website is reputable. One of the easiest ways for attackers to compromise your website is to trick you into loading malware yourself. An attacker will do this by setting up a website that looks legitimate and getting you to download a compromised or ‘nulled’ plugin.
Use these tips to help determine whether a site is a reputable source or not:
- Eye Test – Is the site itself professionally designed and uses clear language to describe the product? Or does it look like it was thrown together quickly by a single individual?
- Company Information – Does the site belong to a company with the company name in the footer?
- TOS and Privacy Policy – Do they have terms of service and a privacy policy?
- Contact Info – Do they provide a physical contact address on the contact page or in their terms of service?
- Domain Search – Google the domain name in quotes e.g. “example.com“. Do you find any reports of malicious activity. Add the word ‘theme’ or ‘plugin’ next to the quoted domain name in your search and see what that reveals.
- Name Search – Do a Google search for the name of the plugin and see if any malicious activity is reported. Add the phrase “malware” or “spyware” to the search which may reveal forums discussing a malicious version of the theme being distributed.
- Vulnerability Search – Do a search for the theme or plugin name or the vendor name and include the word “vulnerability”. This will help you find out if any vulnerabilities have been reported for the product you’re interested in or for the vendor. If they have fixed the vulnerability in a timely manner, that usually indicates they are a responsible vendor who is actively maintaining their product when problems arise.
Brute Force Attacks Are Still A Big Problem
A brute force attack is a password guessing attack. The attacker needs to both identify a valid username on your website and then guess the password for that username. Despite the availability of methods and technology that are 100% effective, this type of attack is still a huge problem, representing 16.1% of known entry points in our survey.
Some tips for avoid a hack via brute force attack:
Use Cellphone Sign-in
Also referred to as two factor authentication, this approach requires the user to not only know their password, but to have possession of their cell phone as well. This technology is 100% effective in preventing brute force attacks. Wordfence premium includes this feature today.
Don’t Use Obvious Usernames
The most obvious usernames to avoid are ‘Admin’ and ‘Administrator’, they are the most common usernames attempted in brute force attacks. Also avoid using your domain name, company name and the names of people who are writing for your blog or are listed elsewhere on your website.
Enable Login Security in Wordfence
The free version of Wordfence provides a long list of login security features. By making sure they are enabled, you benefit from the following features:
- Enforce strong passwords
- Locking users out after a defined number of login failures
- Locking out users after a number of forgot password attempts
- Locking out invalid usernames
- Preventing WordPress from revealing valid usernames in login errors
- Preventing username discovery through author scans
- Immediate blocking of IPs that try to sign in as a defined list of usernames.
Other Steps to Secure your Site
Keeping everything up-to-date is key. There are no serious known vulnerabilities in the current version of WordPress core. There are however, a large number of known vulnerabilities in older WordPress versions. So keeping WordPress core up-to-date is very important. The WordPress team responds quickly when an issue is reported and so should you.
Many of our respondents indicated that their hosting account was compromised in some way. Make sure that you have a strong password policy for your CPanel account and any other server or hosting related accounts. Also ensure that you remove any applications on your server, like phpmyadmin, that aren’t absolutely necessary. If you don’t, you will have to maintain them too and ensure they’re updated and secure. Each application is another endpoint that can be attacked. The less you have to protect, the lower your risk.
Secure your workstation by keeping your operating system and applications up-to-date. Running an old vulnerable web browser, or an old version of Flash or Adobe reader can make you vulnerable to phishing attacks that can compromise your workstation. Once you workstation is compromised, an attacker can easily install a keyboard logger to capture usernames and passwords. They will gain access to much more than your WordPress website.
Store passwords securely. Do not store them in plaintext in a document online that may be compromised. You can use a product like 1Password which provides an encrypted ‘vault’ to store your passwords in.
Finally, as we’ve said before, delete any old data you don’t need from your website. This includes backup files you don’t need, log files, applications you don’t use or anything else you don’t need on your site. Old data is one more possible entry point that needs to be protected and if you can remove it, you reduce risk.
Conclusion
WordPress security is a battle fought on many fronts, as evidenced by the 42 items on our checklist and the depth and breadth of subjects in our ever evolving Learning Center. But knowledge is power, and this survey data allows us to focus on what matters most. We hope that you take the opportunity to make improvements in how you select and manage plugins on your website. We also hope that you review your approach to brute force attack protection. Small investments in these areas will pay big security dividends. Stay safe!
The post How Attackers Gain Access to WordPress Sites appeared first on Wordfence.
